“Severe” ransomware attack cripples big aluminum producer

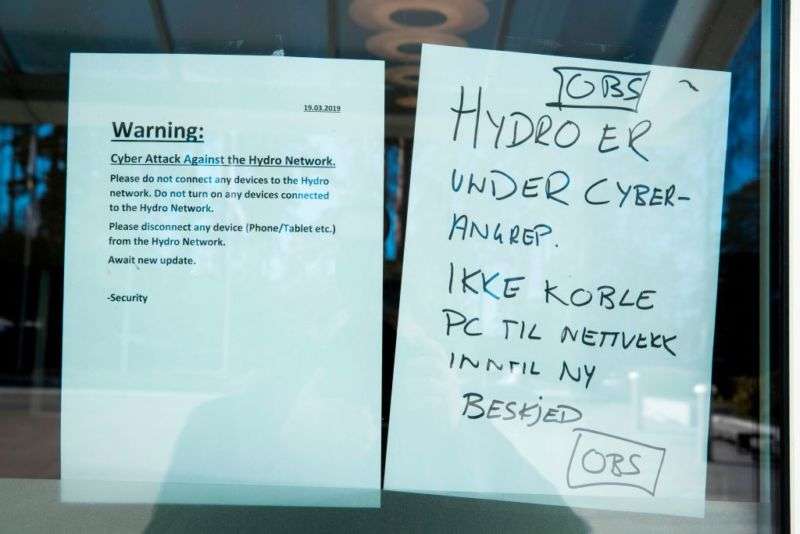
One of the world’s biggest producers of aluminum has been hit by a serious ransomware attack that shut down its worldwide network, stopped or disrupted plants, and sent IT workers scrambling to return operations to normal.
Norsk Hydro of Norway said the malware first hit computers in the United States on Monday night. By Tuesday morning, the infection had spread to other parts of the company, which operates in 40 countries. Company officials responded by isolating plants to prevent further spreading. Some plants were temporarily stopped, while others, which had to be kept running continuously, were switched to manual mode when possible. The company’s 35,000 employees were instructed to keep computers turned off but were allowed to use phones and tablets to check email.
“Let me be clear: the situation for Norsk Hydro through this is quite severe,” Chief Financial Officer Eivind Kallevik said during a press conference Tuesday. “The entire worldwide network is down, affecting our production as well as our office operations. We are working hard to contain and solve this situation and to ensure the safety and security of our employees. Our main priority now is to ensure safe operations and limit the operational and financial impact.”
According to Kevin Beaumont, tweeting in his capacity as an independent researcher and citing local media reports, the ransomware that infected Norsk Hydro is known as LockerGoga. He said LockerGoga doesn’t rely on the use of network traffic or on domain name system or command and control servers, traits that allow the ransomware to bypass many network defenses. An independent research group calling itself MalwareHunterTeam pointed to this LockerGoga sample uploaded to VirusTotal from Norway on Tuesday morning. At the time the malware was first scanned, it was detected by only 17 of the 67 biggest AV products, although detections increased once awareness of the Norsk Hydro infection grew. The malware had also once been digitally signed by security company Sectigo, but the certificate was revoked at an unknown time.
A text file that attackers included with the malware included the following:
There was a significant flaw in the security system of your company. You should be thankful that the flaw was exploited by serious people and not some rookies. They would have damaged all your data by mistake or for fun.
Your files are encrypted with the strongest military algorithms RSA4096 and AES-256. Without our special decoder it is impossible to restore that data. Attempts to restore your data with third-party software as Photorec, RannohDecryptor etc. will lead to irreversible destruction of your data.
The note went on to offer the decryption of up to three files chosen by the reader to prove the authenticity of the claim. It also demanded a ransom of an unspecified amount payable in bitcoin.
During Tuesday’s press conference, an official with the Norwegian National Security Authority stopped short of confirming Norsk Hydro was infected by LockerGoga, saying only that it was a “one of the theories.” LockerGoga may have been used two months ago to infect the systems of French engineering consultancy Altran, Bleeping Computer reported.
Norsk Hydro shares traded down about 0.7 percent following the report of the infection. Aluminum futures on the London Metal Exchange rose in line with other metals, Bloomberg News reported
While Kallevik, the Norsk Hydro CFO, said the majority of the company’s plants were operating normally, he said the network shutdown prevented plants from receiving future orders from customers. He said the losses at the moment were “minimal,” but he conceded they would grow over time if automated systems aren’t restored. Kallevik was unable to provide any timetable for how long it would take to disinfect the network.
He said company IT teams are working to remove the ransomware from infected systems. Once that’s done, the teams plan to restore lost data using company backup systems, which Kallevik described as “good.” Asked by a reporter if the company would rule out paying the demanded ransom, the CFO said the “main strategy is to use backup.”




