Self-driving car service open sources new tool for securing firmware

Developing and maintaining secure firmware for tablets, cars, and IoT devices is hard. Often, the firmware is initially developed by a third party rather than in-house. And it can be tough as projects move from inception and prototyping to full-force engineering and finally to deployment and production.
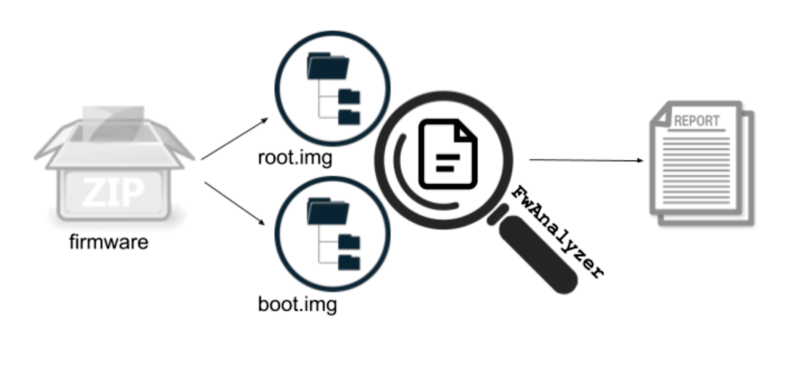
Now, an engineer at self-driving car service Cruise is easing the pain with the release of FwAnalyzer, a tool he and his Cruise colleagues developed themselves. Collin Mulliner spent more than a decade scouring firmware found in phones and other devices before becoming Cruise’s principal security engineer. He helped write FWAnalyzer to provide continuous automated firmware analysis that could aid engineers at any phase of the code’s lifecycle.
“It’s peace of mind that there’s constant analysis,” Mulliner said of the tool, which he’ll be discussing at a panel on Wednesday at the Black Hat security conference in Las Vegas. “At any step in development… it runs checks.”
The tool has a menu of configuration rules engineers can select to tailor the analysis. The options include rules that are applied to file metadata such as permissions, type and ownership, rules that target the content of a file, and rules that analyze file system metadata. They can be used to detect SETUID files to help identify potentially dangerous executables. They can also be used to identify any debugging code that was mistakenly left behind. That can help prevent hackers from later misusing that code. The full capabilities go well beyond that.
“Armed with these capabilities, you now have the ability to detect and prevent a wide variety of security issues,” Mulliner wrote in a post accompanying Wednesday’s talk. “Using an external script that we provide, you can detect any non-stripped binaries, preventing leaking potentially valuable debug information.”




