Patch Windows 10 and Server now because certificate validation is broken

Microsoft’s scheduled security update for Windows includes a fix to a potentially dangerous bug that would allow an attacker to spoof a certificate, making it look like it came from a trusted source. The vulnerability, reported to Microsoft by the National Security Agency, affects Windows 10, Windows Server 2016, Windows Server 2019, and Windows Server version 1803.
Microsoft has rated the update as “important” rather than critical. But in a blog post, Mechele Gruhn, the Principal Security Program Manager for Microsoft Security Response Center, explained that this was because “we have not seen it used in active attacks.”
However, researchers outside Microsoft—including Google’s Tavis Ormandy—have a much more dire assessment of the vulnerability and urge users to patch quickly before an active exploit appears.
Will confirms all X.509 validation broken, not just code signing. Okay, I’m back on the hype train, that’s pretty bad. https://t.co/6rBV1lu4Yk
— Tavis Ormandy (@taviso) January 14, 2020
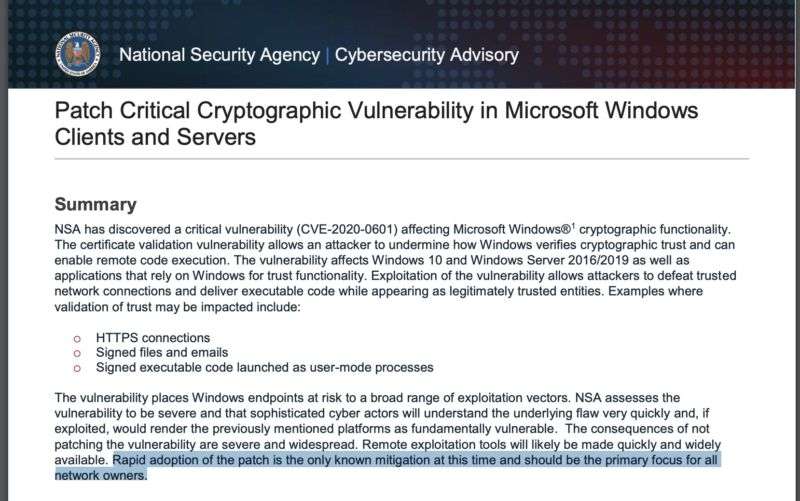
The vulnerability is in the component of Windows’ cryptography library that validates X.509 certificates, somehow bypassing the chain of trust used to validate the certificate. Microsoft’s advisory on the vulnerability said that the bug could be used to fake the software-signing certificate on a malicious version of an application, making it look like it came from a trusted developer. However, the risk extends beyond just code-signing. A National Security Agency advisory indicates that the vulnerability could be used for man-in-the-middle attacks against secure HTTP (HTTPS) connections, as well, and to spoof signed files and emails.
The NSA advisory is much more helpful than Microsoft’s. https://t.co/6JxeHDPgPP
— Tavis Ormandy (@taviso) January 14, 2020
It’s possible to perform network-level protection against spoofed certificates using network devices that inspect TLS traffic—as long as they don’t use Windows’ certificate validation. But the NSA warned, “Rapid adoption of the patch is the only known mitigation at this time and should be the primary focus for all network owners.”
Of course, there are plenty of other things that are more pressing, we know—like all those Citrix and Pulse Secure VPNs that haven’t been patched yet.
Now back to those hundreds of unpatched government SSL VPN boxes which are actively being exploited and drop you right inside the network and give you valid credentials.
— Kevin Beaumont (@GossiTheDog) January 14, 2020
The bottom line is: install the patch. Don’t delay.




