New “red team as a service” platform aims to automate hacking tests for company networks

Attack simulation and “red teaming as a service” have become a hot area of development over the past few years as companies continue to seek ways to better train their network defenders and find problems before attackers do. Randori, a company pulling together red-teaming skills and security software experience, today is launching a new platform that attempts to capture the expertise of a high-budget security testing team as a cloud-based service—giving chief information security officers a way to continuously take the pulse of their companies’ defenses.
Red teaming, the practice of actively researching and exploiting vulnerabilities in systems to help find and fix gaps in their security, has long been the realm of high-paid security consulting firms with hands-on-keyboard (and occasionally, with full penetration testing, hands-on-lockpick) engagements, and not something most companies can afford to do regularly. Large organizations and software firms with a business imperative to keep their systems secure have typically maintained internal red teams, but smaller organizations that need red teams for things like getting credit card compliance certification or checking the security of other financial systems often rely on hit-and-run engagements with outside specialists.
There have been other efforts to streamline and automate components of red teaming to make it a more regular part of companies’ security programs. For example, Scythe, a firm that spun out of the security research company Grimm, has focused on providing attack simulation as a service—allowing a company to test the mettle of its “blue team” defenders and users by running modular “attacks” that mimic the techniques of known threat groups, while creating a marketplace for security testing modules. And other companies, such as Pwnie Express, have used passive and “offensive” security tools to scan and audit networks for potential attack vectors.
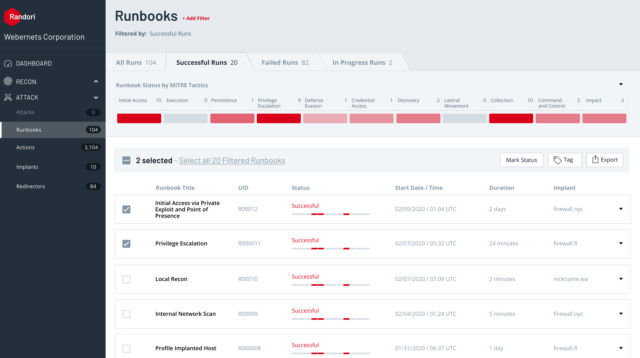
Randori takes the red-teaming mission several steps further. Instead of running simulations of attacks based on known threats, Randori Attack runs real, novel attacks based on emerging vulnerabilities—much like a human red team would. Founded by CEO Brian Hazzard (formerly of Carbon Black) and CTO David “Moose” Wolpoff (a reverse-engineering and red-teaming veteran of the specialist security firm Kyrus Tech), Randori’s “flagship” service is the Attack Platform—a cloud-based system that, when combined with Randori’s Internet-based reconnaissance system, will constantly discover and attempt to exploit a customer company’s system, playing the role of what Hazzard describes as “trusted adversary.”
The inspiration for Randori began while Hazzard was vice president of product management at Bit9, the company that would acquire the original Carbon Black in 2013 and later take its name. Bit9 was hit by a nation-state backed cyberattack in 2012, in which the attacker leveraged the company’s software reputation service and certificates to distribute malware to targeted customers. “After we got hacked, we made a huge investment in cybersecurity,” Hazzard told Ars, “but that clearly wasn’t enough.”
Hazzard’s team brought in Wolpoff’s company to “come at us at a nation-state level” to help harden its defenses. “Moose came after us hard, and we learned a two things started happening—we got a much better handle on what our attack surface was, and we got a way better understanding and more effective at protecting our crown jewels—that was important to the business.”
In 2018, Hazzard left Carbon Black, which was acquired by VMWare (a deal that completed in October of 2019). “I knew I was going to start another company and knew [the red-teaming business] needed to be modernized,” he said. Hazzard reached out again to Wolpoff with the idea of bringing software-as-a-service scalability to the security-testing world. “We’re trying to get the red-team experience in the hands of every CISO,” he said. “How do you build defenses if you don’t know how the attacker is going to come after you? The whole objective of Randori Attack is that it’s a SaaS platform that mirrors the adversary and how they would come after you.”
Wolpoff explained that the SaaS model allowed for a greater level of investment in research and the development of attacks than the traditional economics of the red-teaming business—”the same level of investment as a state actor.” Instead of building custom tools for each engagement, Randori’s researchers and developers can build a “run book” for each new type of vulnerability that emerges and then convert it into an automated set of software that can be deployed via Kubernetes instances or other cloud-based computing resources to mimic how a real attack would look to their customers.
Randori’s reconnaissance system and the Attack platform work together to continuously scan for, discover, and exploit weaknesses in customers’ networks from the outside, allowing CISOs to control the scope of tests dynamically as new vulnerabilities are discovered. All of the service is manageable through a Web console, with a dashboard that alerts security teams to the latest findings made by Attack.
Greenhill & Co., a New York-based independent investment bank, is one of Randori’s early customers, and it’s an example of the kind of company Randori is targeting for its product—a company with about 500 employees in an industry that has the need for strong security, but without the resources for an internal red team. “Red team engagements are the gold standard in security testing, but they are too expensive to do frequently,” said John Shaffer, Greenhill’s CIO, in a statement provided by Randori. “Randori’s automated methodology bridges the gap, giving me the ability to continuously test my tools, people and processes against real-world scenarios. Over the past year, Randori has greatly enhanced my visibility into our security stack and been an agent to change our internal culture of security.”