Mass router hack exposes millions of devices to potent NSA exploit

More than 45,000 Internet routers have been compromised by a newly discovered campaign that’s designed to open networks to attacks by EternalBlue, the potent exploit that was developed by, and then stolen from, the National Security Agency and leaked to the Internet at large, researchers said Wednesday.
The new attack exploits routers with vulnerable implementations of Universal Plug and Play to force connected devices to open ports 139 and 445, content delivery network Akamai said in a blog post. As a result, almost 2 million computers, phones, and other network devices connected to the routers are reachable to the Internet on those ports. While Internet scans don’t reveal precisely what happens to the connected devices once they’re exposed, Akamai said the ports—which are instrumental for the spread of EternalBlue and its Linux cousin EternalRed—provide a strong hint of the attackers’ intentions.
The attacks are a new instance of a mass exploit the same researchers documented in April. They called it UPnProxy because it exploits Universal Plug and Play—often abbreviated as UPnP—to turn vulnerable routers into proxies that disguise the origins of spam, DDoSes, and botnets. In Wednesday’s blog post, the researchers wrote:
Taking current disclosures and events into account, Akamai researchers believe that someone is attempting to compromise millions of machines living behind the vulnerable routers by leveraging the EternalBlue and EternalRed exploits.
Unfortunately, Akamai researchers are not able to see what happens after the injections have occurred, they can only see the injections themselves and not the final payloads that would be directed at the machines exposed. However, a successful attack could yield a target rich environment, opening up the chance for such things as ransomware attacks, or a persistent foothold on the network.
Currently, the 45,113 routers with confirmed injections expose a total of 1.7 million unique machines to the attackers. We’ve reached this conclusion by logging the number of unique IPs exposed per router, and then added them up. It is difficult to tell if these attempts led to a successful exposure as we don’t know if a machine was assigned that IP at the time of the injection. Additionally, there is no way to tell if EternalBlue or EternalRed was used to successfully compromise the exposed machine. However, if only a fraction of the potentially exposed systems were successfully compromised and fell into the hands of the attackers, the situation would quickly turn from bad to worse.
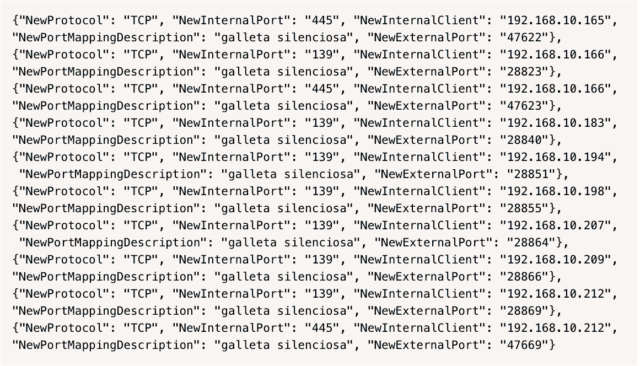
The new instance, which Akamai researchers have dubbed EternalSilence, injects commands into vulnerable routers that open ports on connected devices. Legitimate injections often include a description such as “Skype.” EternalSilence injections use the description “galleta silenciosa”—”silent cookie/cracker” in Spanish. The injections look like this:
A scourge called UPnP
Wednesday’s post is only the latest piece of concerning news to involve UPnP, a protocol that is designed to make it easy for connected devices to operate by using code that lets them automatically discover each other and open ports needed to connect to the outside Internet. Two weeks ago, a separate team of researchers reported UPnP flaws were exploited to spawn a 100,000-router botnet used to send spam and other types of malicious email. Most if not all of the exploited vulnerabilities have been public knowledge since 2013, when a landmark Internet scan found 81 million IPv4 addresses responded to standard UPnP discovery requests, even though the standard isn’t supposed to communicate with devices that are outside a local network.
EternalBlue is an attack developed and used by the NSA that exploited server message-block implementations in Vista and all later versions of Windows. In April 2017, a mysterious group calling itself the Shadow Brokers made the attack code available to the world at large. A month later, EternalBlue was folded into WannaCry, a quick-spreading ransomware worm that paralyzed hospitals, shipping companies, and train stations around the globe. A month later, a disk-wiper dubbed NotPetya also used EternalBlue as an engine to self-replicate extremely rapidly.
While fixes for EternalBlue and EternalRed have been in place for more than a year, some organizations have yet to install them. Failing to patch doesn’t automatically mean a network is vulnerable. If ports are adequately restricted, exploits may not be able to spread. Akamai researchers say the new attacks are likely an opportunistic attempt to open devices to attacks they otherwise would be resistant to.
“The goal here isn’t a targeted attack,” they wrote. “It’s an attempt at leveraging tried-and-true off-the-shelf exploits, casting a wide net into a relatively small pond, in the hopes of scooping up a pool of previously inaccessible devices.”
To prevent attacks, people should ensure their routers aren’t vulnerable to UPnP attacks, either by buying new hardware or ensuring their older device is running updated firmware. Once a router has been exploited by UPnProxy, devices should be rebooted or, better yet, reset to their original factory settings to ensure port forwarding injections are cleared. People with compromised routers should also thoroughly inspect connected devices to ensure they haven’t been infected.