Loose online lips sink hack targeting governments and embassies

Security researchers gave mixed grades to a recently discovered hacking campaign targeting government finance authorities and embassies. On the one hand, the attacks used carefully crafted decoy documents to trick carefully selected targets into installing malware that could gain full control of computers. On the other, a developer involved in the operation sometimes discussed the work in public forums.
The campaign has been active since at least 2018 when it sent Excel documents claiming to contain top-secret US data to people inside governments and embassies in Europe, security firm Check Point reported in a post published Monday. Macros in the documents would send a screenshot and user details of the target’s PC to a control server and then install a malicious version of TeamViewer that claimed to offer additional functionality. The trojan would then gain complete control over the infected computer.
A poorly secured control server allowed Check Point researchers to periodically see screenshots that were uploaded from infected computers, at least until the server was locked down. Most of the targets had a connection to public finance and government officials from revenue authorities. Using the intercepted images and telemetry data, Check Point researchers compiled a partial list of countries where targets were located. It included:
- Nepal
- Guyana
- Kenya
- Italy
- Liberia
- Bermuda
- Lebanon
The payload in the Excel documents changed at least three times over the course of the last one or more years. What Check Point had found, then, was a hacking campaign that, despite a control server that initially made available collected screenshots, had nonetheless succeeded in infecting computers used in governments and embassies.
Enter EvaPiks
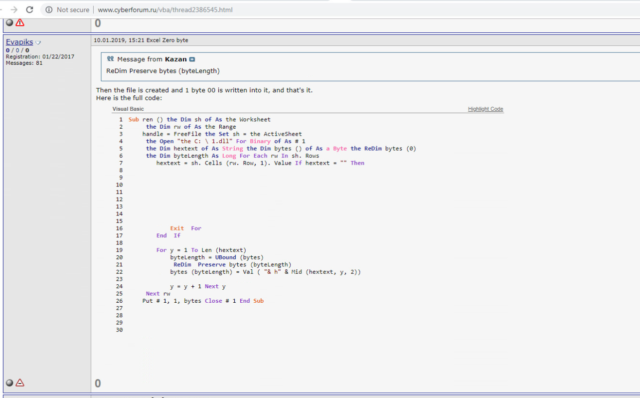
But soon, Check Point researchers found something else—an online persona who had a demonstrated connection to the operation. Using the moniker EvaPiks, the Russian-speaking person on several occasions posted code and techniques used in the operation.
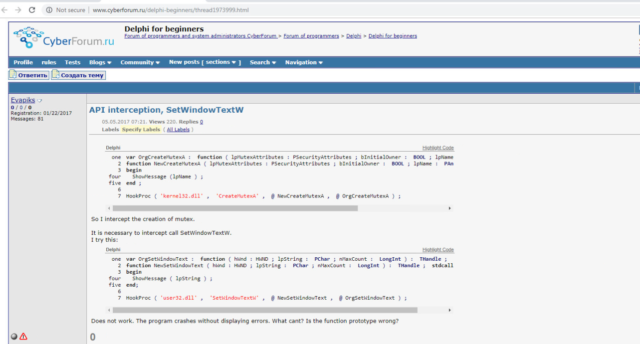
The macro code shown in the post above—including the variable name “hextext”—was used in one of the actual attacks. The screenshot below, from a 2017 post in which the user sought advice on API function call interception, discussed a hooking technique of the functions named CreateMutexA and SetWindowTextW.
The same hooking techniques are present in samples analyzed by Check Point. Check Point found that the same persona was active on an illegal Russian carding forum. The researchers say that EvaPiks’ interest in carding means that the attacks are likely financially motivated, rather than being motivated by espionage.
Monday’s post includes cryptographic hashes of malicious binaries, IP addresses, and document names that serve as indicators of compromise.