Keybase moves to stop onslaught of spammers on encrypted message platform

Keybase started off as co-founder and developer Max Krohn’s “hobby project”—a way for people to share PGP keys with a simple username-based lookup. Then Chris Coyne (who also was cofounder of OkCupid and SparkNotes) got involved and along came $10.8 million in funding from a group of investors led by Andreesen Horowitz. And then things got increasingly more complicated. Keybase aims to make public-key encryption accessible to everyone, for everything from messaging to file sharing to throwing a few crypto-coins someone’s way.
But because of that level of accessibility, Keybase faces a very OkCupid kind of problem: after drawing in people interested in easy public-key crypto-based communications and then drawing in blockchain lovers with its partnership with (and funding from) Stellar.org, Keybase has also drawn in spammers and scammers. And that has brought a host of alerts and messages that have made what was once a fairly clear communications channel into one clogged with unwanted alerts, messages, and other unpleasantry—raising a chorus of complaints in Keybase’s open chat channel.
It turns out there’s a reason spell check keeps wanting to tell me that Keybase should be spelled “debase.”
Full disclosure: I have been a Keybase user for several years, and fellow Ars editor Lee Hutchinson and I had experimented with using Keybase as a potential way of securing some of our workflow. Not needing anyone to host (and therefore own) our data seemed like a good thing. But Lee recently canceled his Keybase account and says he won’t be back because of how annoying it is.
Keybase’s leadership is promising to do something to fix the spam problem—or at least make it easier to report and block abusers. In a blog post, Krohn and Coynes wrote, “To be clear, the current spam volume isn’t dire, YET. Keybase still works great. But we should act quickly.”
But the measures promised by Keybase won’t completely eliminate the issue. And Keybase execs have no interest in getting involved with additional steps that they see as censorship. “Keybase is a private company and we do retain our rights to kick people out,” the co-founders said in the blog post. “That hammer will not be used because someone is mostly disliked, as long as they’re playing nicely on Keybase.”
Romancing the scam
Part of the attraction of Keybase is that it allows hassle-free access from the Tor anonymizing network, as well as from VPNs—which makes it harder to track down the source of abusive traffic through the service. But much of the spam traffic is over unobfuscated network connections, and while some of it is coming from Europe and North America, most is coming from Russian and Nigerian IP addresses.
Other platforms have seen the same sort of problem. Romance scammers got their start on instant messaging platforms and quickly moved on to dating apps. Earlier this decade, OkCupid became a den for these scams—where someone (often in Nigeria) poses as someone looking for love, and then moves the conversation toward pleas for financial support, calling cards, or other investments. And as I’ve reported earlier this year, these and other scams have taken hold on Twitter.
Right now, it’s possible (with some navigation) to block someone from messaging you on Keybase and hiding messages they send. But there’s no effective way to report them for abuse other than reaching out to administrators directly. And there’s no way to completely filter out the requests in the first place, as anyone can create a Keybase account and send a message to you.
-
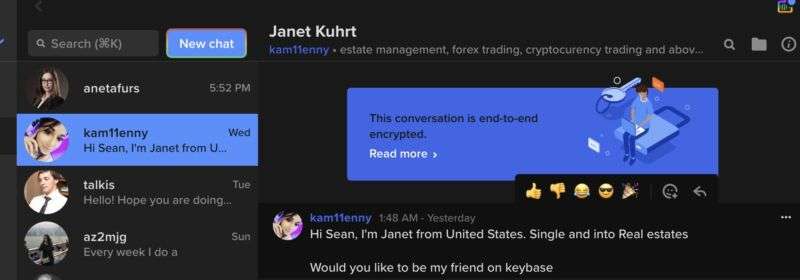
A romance scammer hits me up.
-
I’m sure this is legit.
-
Sure you are.
-
This profile uses a Twitter account to verify, but…
-
That Twitter account sure is convincing.
Talk to the block
As part of the changes to Keybase being pushed out in an upcoming release, users will now be able to report spam or abusive messages straight from Keybase’s chat interface—blocking that user with a click or tap, with the option of reporting the user to Keybase administrators. The report allows for quick classification of the message as spam, harassment, “obscene material,” or “other,” with a field for additional details. “You’ll also be able to send Keybase admins the transcript of your chat—something we obviously don’t normally have access to, since Keybase is end-to-end encrypted,” Keybase execs explained in their post.
Another measure Keybase calls the “nuclear option” is also in the works. Similar to Twitter’s protected account capabilities, it allows users to select a set of rules that determine who can follow or message them—based on whether they’re already connected in some way.” These options will create a custom walled-garden experience,” the Keybase execs explained. “It won’t be necessary for most people — especially after the blocking features launch — but it will 100% shut down all unwanted contact.”
More fixes are promised in the future. Considering that Keybase already provides ways for people to attest to their identities to provide trust in communications, it would be conceivable that you could filter requests based on the quality and number of those attestations—confirmations made by posting messages to social media accounts, GitHub accounts, and other accounts that are connected to online identity (mine is tied to Twitter, GitHub, Hacker News, Reddit, and a personal domain name as well as my PGP key). Most fraudulent accounts don’t bother with anything more than the free Stellar wallet address, and those that do often attach a fake Twitter account.
None of this is going to bring Lee Hutchinson back. “When a tool that I don’t need or think about very often starts spamming me and requires I dig up documentation to make the spamming stop,” Lee said, “I’m not going to take time out of my [redacted] day to read the docs and screw around with privacy settings. I’m just going to delete the tool. Which I did.”




