I’ve got a bridge to sell you. Why AutoCAD malware keeps chugging on

Criminal hackers continue to exploit a feature in Autodesk’s widely used AutoCAD program in an attempt to steal valuable computer-assisted designs for bridges, factory buildings, and other projects, researchers said Tuesday.
The attacks arrive in spear-phishing emails and in some cases postal packages that contain design documents and plans. Included in the same directory are camouflaged files formatted in AutoLISP, an AutoCAD-specific dialect of the LISP programming language. When targets open the design document, they may inadvertently cause the AutoLISP file to be executed. While modern versions of AutoCAD by default display a warning that a potentially unsafe script will run, the warnings can be disregarded or suppressed altogether. To make the files less conspicuous, the attackers have set their properties to be hidden in Windows and their contents to be encrypted.
The attacks aren’t new. Similar ones occurred as long ago as 2005, before AutoCAD provided the same set of robust defenses against targeted malware it does now. The attacks continued to go strong in 2009. A specific campaign recently spotted by security firm Forcepoint was active as recently as this year and has been active since at least 2014, an indication that malware targeting blueprints isn’t going away any time soon.
In an analysis expected to be published Wednesday, company researchers wrote:
CAD changed our modern life and, as an unfortunate side effect, industrial espionage also changed along with it. Design schemes, project plans, and similar vital documents are being stored and shared between parties in a digital manner. The value of these documents–especially in new and prospering industries such as renewable energy–have probably never been this high. All this makes it attractive for the more skilled cybercriminal groups to chip in: instead of spamming out millions of emails and waiting for people to fall for it, significantly more money can be realized by selling blueprints to the highest bidder.
Forcepoint said it has tracked more than 200 data sets and about 40 unique malicious modules, including one that purported to include a design for Hong Kong’s Zhuhai-Macau Bridge. The attacks include a precompiled and encrypted AutoLISP program titled acad.fas. It first copies itself to three locations in an infected computer to increase the chances it will be opened if it spreads to new computers. Infected computers also report to attacker-controlled servers, which use a series of obfuscated commands to download documents.

All of the control server subdomains resolve to the same IP address, which appears to be running a Chinese-language installation of Microsoft Internet Information Server 6.0. Forcepoint researchers found that the same IP was used in earlier AutoCAD campaigns. They also found a neighboring IP that had the same IIS configuration.
Multiple companies in multiple locations
“Pivoting on the C2 domains suggests that the actors have successfully targeted multiple companies across multiple geolocations with at least one campaign likely having been focused on the energy sector,” Forcepoint researchers wrote. “Several companies either within or with links to the renewable energy industry appear to have fallen victim to the malware.”
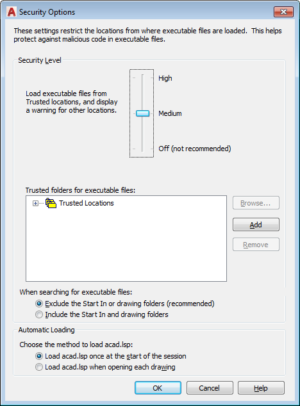
As noted earlier, AutoCAD has added a variety of mitigations to prevent these sorts of attacks. Chief among them is a security options box that controls what executable files can be loaded, from what locations, and whether a warning popup should be displayed. The best option is to disable auto-executing files altogether. If that’s not feasible, the locations of files should be tightly restricted, and warnings should always be displayed. Users should also consider configuring Windows to show all files, even when their attributes are set to ‘hidden.’