Hackers breached 3 US antivirus companies, researchers reveal

In a report published Thursday, researchers at the threat-research company Advanced Intelligence (AdvIntel) revealed that a collective of Russian and English-speaking hackers are actively marketing the spoils of data breaches at three US-based antivirus software vendors. The collective, calling itself “Fxmsp,” is selling both source code and network access to the companies for $300,000 and is providing samples that show strong evidence of the validity of its claims.
Yelisey Boguslavskiy, director of research at AdvIntel, told Ars that his company notified “the potential victim entities” of the breach through partner organizations; it also provided the details to US law enforcement. In March, Fxmsp offered the data “through a private conversation,” Boguslavskiy said. “However, they claimed that their proxy sellers will announce the sale on forums.”
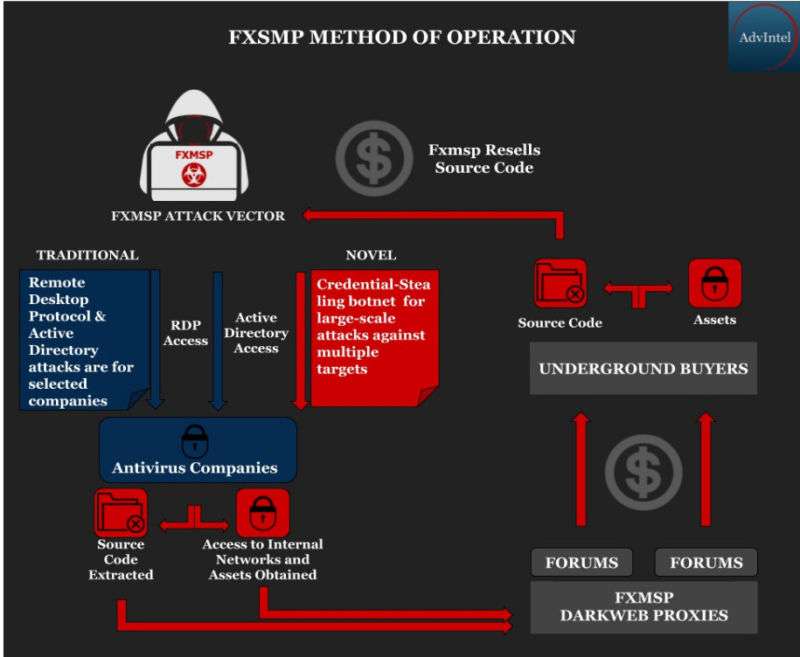
Fxmsp has a well-known reputation in the security community for selling access to breaches, focusing on large, global companies and government organizations. The group was singled out in a 2018 FireEye report on Internet crime for selling access to corporate networks worldwide, including a global breach of a luxury hotel group—potentially tied to the Marriott/Starwood breach revealed last November. AdvIntel’s researchers say the group has sold “verifiable corporate breaches,” pulling in profits approaching $1 million. Over the past two years, Fxmsp has worked to create a network of proxy resellers to promote and sell access to the group’s collection of breaches through criminal marketplaces.
In March, the group “stated they could provide exclusive information stolen from three top antivirus companies located in the United States,” AdvIntel’s researchers reported in a blog post going live today. “They confirmed that they have exclusive source code related to the companies’ software development.” And the group offered privately to sell the source code and network access to all three companies for “over $300,000,” the researchers said.
According to the AdvIntel report, Fxmsp had managed to steal source code that included code for antivirus agents, analytic code based on machine learning, and “security plug-ins” for Web browsers. “Fxmsp also commented on the capabilities of the different companies’ software and assessed their efficiency,” the researchers wrote.
In the past, Fxmsp’s breaches have typically focused on exploiting Internet-connected remote desktop protocol (RDP) and Active Directory servers. But more recently, the group has claimed to have developed a credential-stealing botnet—malware that collects usernames and passwords—to target high-value networks that are better secured. “Fxmsp has claimed that developing this botnet and improving its capabilities for stealing information from secured systems is their main goal,” AdvIntel’s researchers noted.
Update:
Boguslavskiy provided some additional details about the breach research in response to follow-up questions (and some of the feedback on this story). He said that AdvIntel first notified the FBI “through both Cyber Watch and the New York Cyber Task Force”.
told Ars that in October of 2018, Fxmsp “had a conflict with their proxy seller, and this relationship was compromised.” Since the proxy monitored Fmsp’s accounts on the various forums that the group typically sold its data through, this caused Fxmsp to move all its communications to Jabber instant messaging.





