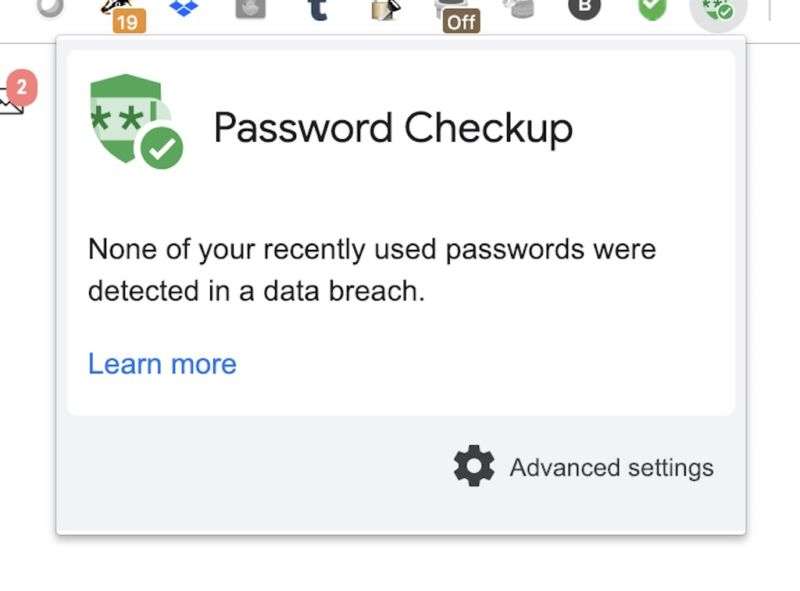
Google releases Chrome extension that alerts users of breached passwords

With lists of billions of compromised credentials floating around on underground forums and in text-paste pages across the Internet, it’s difficult for anyone to keep up with the potential threat from breached passwords. That’s why, as part of its security efforts during Safer Internet Week, Google has released a new add-on for the Chrome browser that automatically and securely checks website credentials against known password breaches.
The Chrome browser extension, called Password Checkup, is available today. It securely checks credentials used to log in to websites—whether they’re manually entered or stored in Chrome’s password manager—against hashed credentials stored in an encrypted database of billions of compromised accounts maintained by Google. Elie Bursztein, head of Google’s anti-abuse research, told Ars that the protocol behind the service is being presented as a standard for securely checking account security and that the interface may be offered as an open application interface in the future.
Checking for password breaches is a sensitive operation. Google’s security team has been offering password checks for G Suite users for some time, but doing the same thing for the rest of users’ credentials is a much more delicate privacy dance. Users don’t want to just hand over their passwords and accounts to Google openly, and “Google has a data set we don’t want to publicly share,” said Kurt Thomas, staff research scientist at Google. So Password Checkup uses a combination of anonymization and cryptography to protect the exchange, using a technique called “blinding” to create a secret search index. Credentials are anonymized with an Argon2 hash function to create a search key for Google’s database and encrypted with Elliptic Curve cryptography.
“On your end, you get an index that only you know,” said Thomas. And that index is both hashed and only a partial encoding of the information—it can’t be used to recreate a complete version of login credentials.
The backend database contains data culled from password dumps on underground marketplaces. Currently, it contains terabytes of data on over 20 billion compromised credentials and is constantly being updated by Google’s threat research team, Bursztein said. The database and the API to access it could be applied to a number of future capabilities, and Bursztein said that his team is open to suggestions on how to best use it. Potentially, the database could be a valuable resource to companies’ internal threat-hunting teams seeking hints of compromise of critical accounts on third-party services. But for now, Bursztein said, the goal is to reach Internet users in a way that’s transparent and easy to use, regardless of whether they have a security team to back them up.




