Bluetooth harvester signals hacking group’s growing interest in mobile

A Korean-speaking hacking group in operation since at least 2016 is expanding its arsenal of hacking tools to include a Bluetooth-device harvester in a move that signals the group’s growing interest in mobile devices.
ScarCruft is a Korean-speaking advanced persistent threat group that researchers with security firm Kaspersky Lab have been following since at least 2016. At the time, the group was found using at least four exploits, including an Adobe Flash zeroday, to infect targets located in Russia, Nepal, South Korea, China, India, Kuwait, and Romania.
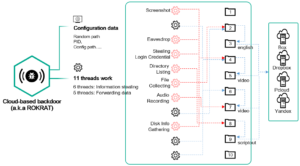
In a post published Monday, Kaspersky Lab researchers said they discovered a custom Bluetooth-device harvester created by ScarCruft. The researchers wrote:
This malware is responsible for stealing Bluetooth-device information. It is fetched by a downloader and collects information directly from the infected host. This malware uses Windows Bluetooth APIs to find information on connected Bluetooth devices and saves the following information.
- Instance Name: Name of device
- Address: Address of device
- Class: Class of the device
- Connected: Whether the device is connected(true or false)
- Authenticated: Whether the device is authenticated(true or false)
- Remembered: Whether the device is a remembered device(true or false)
The attackers appear to be increasing the scope of the information collected from victims.
Overlap with DarkHotel
Kaspersky Lab researchers said that some of the Russia- and Vietnam-based investment and trading companies infected by ScarCruft may have links to North Korea. The researchers said ScarCruft also attacked a diplomatic agency in Hong Kong and another diplomatic agency in North Korea. “It appears ScarCruft is primarily targeting intelligence for political and diplomatic purposes,” the researchers wrote.
One target from Russia triggered a malware detection alert while staying in North Korea. The alert suggests that it had valuable information about North Korean affairs. ScarCruft infected the target in September 2018. Before that, however, the target had been infected by a different APT group known as DarkHotel and, before that, a different piece of malware known as Konni.
“This is not the first time we have seen an overlap of ScarCruft and DarkHotel actors,” Kaspersky Lab researchers wrote. “They are both Korean-speaking threat actors, and sometimes their victimology overlaps. But both groups seem to have different TTPs (Tactics, Techniques, and Procedures), and it leads us to believe that one group regularly lurks in the other’s shadow.”
ScarCruft infects its targets through spearphishing emails and by infecting the websites they visit and lacing them with exploits. Sometimes, the exploits are zerodays. In other cases, the group has used public exploit code. The group also uses a multi-stage infection process that ultimately downloads files from a command and control server. To thwart network defenses, the downloader uses steganographic techniques that hide an encrypted payload in an image file. The final payload installs a backdoor known as ROKRAT.
Kaspersky’s discovery of the Bluetooth harvester is evidence that ScarCruft is continuing to develop its capabilities.
“The ScarCruft has shown itself to be a highly skilled and active group,” Monday’s post concluded. “It has a keen interest in North Korean affairs, attacking those in the business sector who may have any connection to North Korea, as well as diplomatic agencies around the globe. Based on the ScarCruft’s recent activities, we strongly believe that this group is likely to continue to evolve.”