Armagadd-on redux: Certificate expiration caused Firefox to disable all add-ons

On Friday, the expiration of a Mozilla certificate used to check the signatures of add-on codes in Firefox desktop and Android Web browsers caused a nearly universal failure of Firefox plug-ins and extensions as browsers detected them as invalid and disabled them.
The bug, dubbed “armagadd-on 2.0,” was addressed by a hot-fix issued over the weekend, and a new version of the browser has been pushed out.
This isn’t the first time this sort of thing has happened with Firefox. The original “armagadd-on” happened almost exactly three years ago, on May 2, 2016, when an expired certificate caused signature verification errors for add-ons.
In a blog post about the new situation on May 4, Mozilla’s Kev Needham wrote:
Late on Friday May 3rd, we became aware of an issue with Firefox that prevented existing and new add-ons from running or being installed. We are very sorry for the inconvenience caused to people who use Firefox.
Our team identified and rolled-out a temporary fix for all Firefox Desktop users on Release, Beta, and Nightly. The fix will be automatically applied in the background within 24 hours. No active steps need to be taken to make add-ons work again. In particular, please do not delete and/or re-install any add-ons as an attempt to fix the issue. Deleting an add-on removes any data associated with it, where disabling and re-enabling does not.
The patch was pushed out to most Firefox desktop users on May 5. However, as Needham noted, the fix does not help Firefox ESR or Android users. An update for those browsers is still in the works.
We’ve heard some questions from folks using Firefox Extended Support Release (ESR). The current fix we’re working on does not apply to ESR, but it’s on our radar and we will be releasing corrected versions for ESR as soon as we can.
— Mozilla Add-ons (@mozamo) May 4, 2019
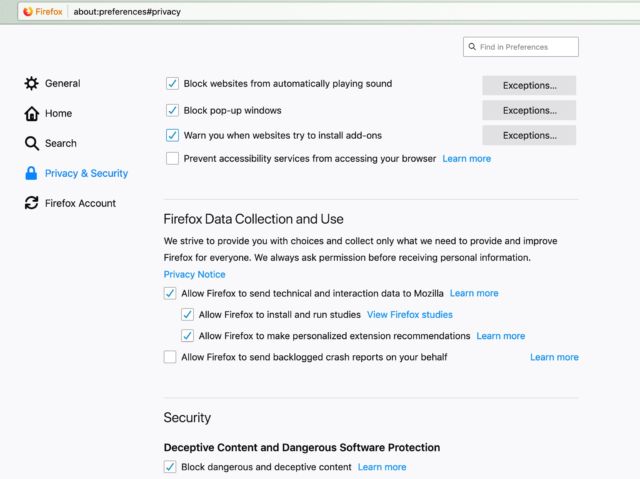
For some users, the patch required them to change browser privacy and security settings before it can kick in—because Mozilla is deploying the patch using Firefox’s “Studies” system to rapidly deploy the patch.
Studies is a system used by Firefox to deploy pre-release features to users before they’re added to a release update. Some organizations and users may disable Studies because they introduce code that hasn’t been tested fully and may send usage data back to Mozilla. But because of the speed with which Mozilla needed to deploy this certificate fix, it was pushed out with Studies rather than as part of a browser update—which means users will have to at least temporarily re-enable Studies to regain functionality. It could take up to six hours for the “hotfix-update-xpi-signing-intermediate-bug-1548973” patch to be applied after Studies are enabled.
Even that didn’t fix the problem for all users, however. Some users reported that their add-ons and extensions were still not re-enabled after turning Studies on. Needham acknowledged that others users reported that even after the hotfix was active, their extensions were still disabled.
“One user has reported success with disabling and re-enabling their extensions,” he noted in the bug report. So far, Mozilla developers have been unable to replicate the bug internally.
Those problems should now be addressed with the new version. But for users who cannot upgrade for other reasons, workarounds may remain the only option.