
Adblockers installed 300,000 times are malicious and should be removed now
If you have Chromium versions of Nano Adblocker or Nano Defender, pay attention. …

reader comments
107 with 88 posters participating, including story author
Adblocking extensions with more than 300,000 active users have been surreptitiously uploading user browsing data and tampering with users’ social media accounts thanks to malware its new owner introduced a few weeks ago, according to technical analyses and posts on Github.
Hugo Xu, developer of the Nano Adblocker and Nano Defender extensions, said 17 days ago that he no longer had the time to maintain the project and had sold the rights to the versions available in Google’s Chrome Web Store. Xu told me that Nano Adblocker and Nano Defender, which often are installed together, have about 300,000 installations total.
Four days ago, Raymond Hill, maker of the uBlock Origin extension upon which Nano Adblocker is based, revealed that the new developers had rolled out updates that added malicious code.
The first thing Hill noticed the new extension doing was checking if the user had opened the developer console. If it was opened, the extension sent a file titled “report” to a server at https://def.dev-nano.com/. “In simple words, the extension remotely checks whether you are using the extension dev tools—which is what you would do if you wanted to find out what the extension is doing,” he wrote.
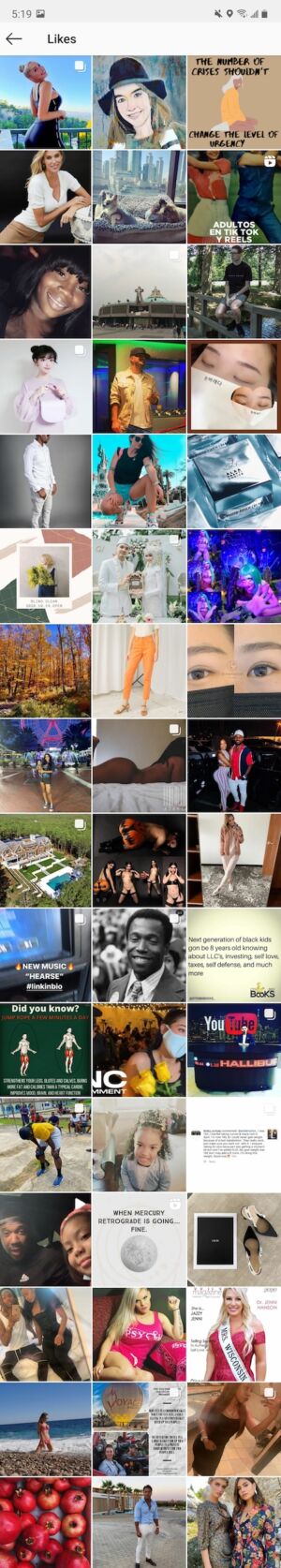
The most obvious change end users noticed was that infected browsers were automatically issuing likes for large numbers of Instagram posts, with no input from users. Cyril Gorlla, an artificial intelligence and machine learning researcher
Continue reading – Article source




