E-commerce site is infected not by one, but two card skimmers

Payment card skimming that steals consumers’ personal information from e-commerce sites has become a booming industry over the past six months, with high-profile attacks against Ticketmaster, British Airways, Newegg, and Alex Jones’ InfoWars, to name just a few. In a sign of the times, security researcher Jérôme Segura found two competing groups going head to head with each other for control of a single vulnerable site.
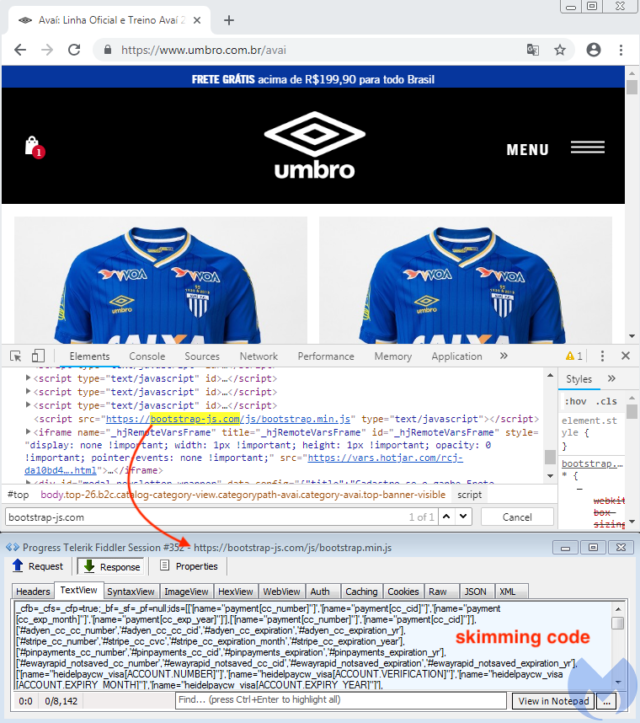
The site belongs to sportswear seller Umbro Brasil, which as of Tuesday morning was infected by two rival skimmer groups. The first gang planted plaintext JavaScript on the site that caused it to send payment card information to the attackers as customers were completing a sale. The malicious JavaScript looked like this:
A second gang exploited either the same or a different website vulnerability as the first. The second group then installed much more advanced JavaScript that was encoded in a way to prevent other programs from seeing what it did. This is what it looked like:
Poisoning the well
The obfuscated JavaScript actively tampered with the less-sophisticated payment skimmer installed by the first gang. Specifically, it replaced the last digit of a credit card number with a randomly generated digit before being sent to the first group. As a result, there was a 90 percent chance that the number obtained by the first group would be incorrect. Because the first group used unobfuscated JavaScript, the skimmer is much more vulnerable to tampering by rivals.
By contaminating the first group’s cache of stolen data with so many bad numbers, the second group is actively—and likely successfully—sabotaging its rival’s operations.
In a blog post published Tuesday, Segura explained:
By tampering with the data, the second skimmer can send an invalid but almost correct credit card number to the competing skimmer. Because only a small part of it was changed, it will most likely pass validation tests and go on sale on black markets. Buyers will eventually realize their purchased credit cards are not working and will not trust that seller again.
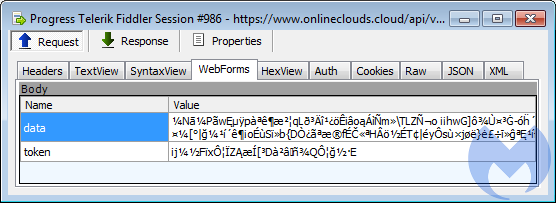
The second skimmer, now being the only one to hold the valid credit card number, uses a special function to encode the data it exfiltrates. Looking at the POST request, we can only see what looks like gibberish sent to its exfiltration domain (onlineclouds[.]cloud):
Encoded data sent back to exfiltration server.Malwarebytes
Joining the Magecart race
The rival gangs are part of “Magecart,” an umbrella term given to multiple crime groups that are racing against each other to infect e-commerce sites with skimmers. A report published last week by security firm RiskIQ counted at least seven such groups, but the actual number is likely higher. This explosion in the number of bad actors is the result of the shift to website-based commerce on poorly secured servers.
The RiskIQ report explained:
The advent of online purchasing altered the global economy, shifting spending away from brick-and-mortar establishments to digital storefronts. Massive online spending gave rise to shopping behemoths such as Amazon and Alibaba, as well as multitudes of small- and medium-sized shops. It also created a space for a new hidden economy to grow around the theft and sale of credit card data.
As with other business supply chains, we see specialization in the criminal cyber community. Software developers create kits for stealing card data from compromised stores but take no part in the actual compromise. They earn money by either selling their kits or entering into profit-sharing agreements with groups or individuals who compromise organizations and then use their kit to inject the skimmer and steal card data. Criminals may compromise stores through their own means, or they may simply purchase access to compromised vendor sites through illicit stores on the Dark Web where such access is sold. The price for each compromised vendor site is set according to its value as determined by those running the illicit stores.
Once the card data is stolen, it must be monetized. There are further illicit stores that specialize in the sale of stolen card data. Presumably, the parties that buy the cards use them to make purchases. Criminal groups may also cut out the middleman and instead recruit unwitting persons to receive goods purchased with stolen card data and re-ship them overseas to the criminal group, who then sell the goods in their home countries.
This economy is currently supporting multiple groups and individuals that have moved to capitalize on the opportunity presented by card theft in the era of online shopping.
The RiskIQ report came a day after Dutch researcher Willem de Groot published a separate analysis reporting that one in five sites that are infected with Magecart skimmers are reinfected after being disinfected. The researcher tracked more than 40,000 infected domains since 2015, 5,400 of them in the past three months.
The reports point to a perfect storm of sorts that’s fueling rampant infections. The difficulty of securing sites and the past successes in infecting big-name sites is encouraging more and more criminal groups to enter the booming field. There’s only so much consumers can do. Steering clear of smaller sites may help, but as the infections of Ticketmaster, British Airways, and Newegg show, larger sites are also being hacked. That leaves monitoring bank statements as the most effective measure most people can take.
At the time this post was going live, Umbro Brasil remained infected by both groups. It’s almost certainly not the only site with this unfortunate distinction.