New flaw neuters Secure Boot, but there’s no reason to panic. Here’s why
Boot Hole provides a new way to install boot-level malware. But it’s hardly the only. …
 reader comments
reader comments
58 with 47 posters participating
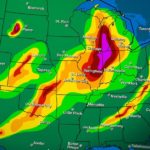
GRUB2, one of the world’s most-widely used programs for booting up computers, has a vulnerability that can make it easier for attackers to run malicious firmware during startup, researchers said on Wednesday. This would affect millions or possibly hundreds of millions of machines. While GRUB2 is mainly used in computers running Linux, attacks that exploit the vulnerability can be performed on many PCs running Windows as well.
The vulnerability, discovered by researchers from security firm Eclypsium, poses yet another serious threat to UEFI Secure Boot, an industry-wide standard that uses cryptographic signatures to ensure that software used during startup is trusted by a computer’s manufacturer. Secure Boot was designed to prevent attackers from hijacking the boot process by replacing the intended software with malicious software.
Stealthier, more powerful, and hard to disinfect
So-called bootkits are among the most serious types of infections because they run at the lowest level of the software stack. That allows the malware to be stealthier than most malware, survive operating system reinstallations, and circumvent security protections built into the OS.
Boot Hole, as the researchers have named the vulnerability, stems from a buffer overflow in the way that GRUB2 parses text in grub.cfg, the boot loader’s main configuration file. By adding long text strings in the file, attackers can overfill the memory space allotted for the file and cause malicious code to spill into other parts of memory, where it then is executed.
The configuration file isn’t digitally signed, so Secure Boot won’t detect when it has been maliciously altered. GRUB2 also doesn’t use address
Continue reading – Article source