Mac users are getting bombarded by laughably unsophisticated malware

Almost two years have passed since the appearance of Shlayer, a piece of Mac malware that gets installed by tricking targets into installing fake Adobe Flash updates. It usually does so after promising pirated videos, which are also fake. The lure may be trite and easy to spot, but Shlayer continues to be common—so much so that it’s the number one threat encountered by users of Kaspersky Labs’ antivirus programs for macOS.
Since Shlayer first came to light in February 2018, Kaspersky Lab researchers have collected almost 32,000 different variants and identified 143 separate domains operators have used to control infected machines. The malware accounts for 30 percent of all malicious detections generated by the Kaspersky Lab’s Mac AV products. Attacks are most common against US users, who account for 31 percent of attacks Kaspersky Lab sees. Germany, with 14 percent, and France and the UK (both with 10 percent) followed. For malware using such a crude and outdated infection method, Shlayer remains surprisingly prolific.
An analysis Kaspersky Lab published on Thursday says that Shlayer is “a rather ordinary piece of malware” that, except for a recent variant based on a Python script, was built on Bash commands. Under the hood, the workflow for all versions is similar: they collect IDs and system versions and, based on that information, download and execute a file. The download is then deleted to remote traces of an infection. Shlayer also uses curl with the combination of options -f0L, which Thursday’s post said “is basically the calling card of the entire family.”
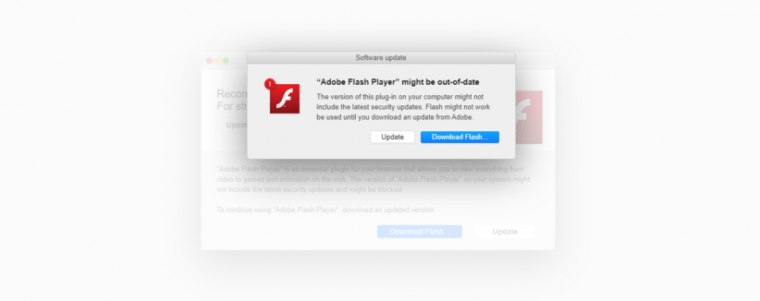
Another banal detail about Shlayer is its previously mentioned infected method. It’s seeded in links that promise pirated versions of commercial software, episodes of TV shows, or live feeds of sports matches. Once users click, they receive a notice that they should install a Flash update. Never mind that Flash has been effectively deprecated for years and that platforms offering warez and pirated content are a known breeding ground for malware.
Second verse, same as the first
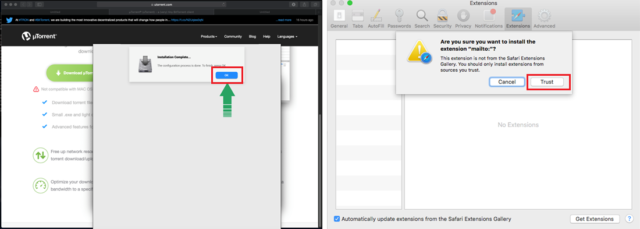
The file downloaded by the Python variant Kaspersky Lab analyzed installs adware known as Cimpli. It ostensibly offers to install applications such as Any Search, which as indicated by search results is clearly a program no one should want. Behind the scenes, it installs a malicious Safari extension and a tool that includes a self-signed TLS certificate that allows the extension to view encrypted HTTPS traffic.
To work around any user suspicions, Cimpli superimposes its own windows over dialog boxes that macOS provides. The left windows in the image below are what targeted users see when Cimpli is installing the Safari extension. The window to the right is what’s covered up. By clicking on the button, the user unwittingly agrees to install the extension. The HTTPS decryption tool also superimposes a fake window over the installation confirmation box. Once installed, all user traffic is redirected to an attacker-controlled proxy server.
Shlayer traditionally has relied on paid affiliates to seed advertising landing pages that display the fake Flash updates. Kaspersky Lab said Shlayer offers some of the highest rates. A newer ploy is the embedding of malicious links in pages on Wikipedia and YouTube. Kaspersky Lab said a single affiliate did so by registering more than 700 expired domains.
It’s hard to believe that malware this artless would be among the most common threats facing Mac users. One explanation may be that Shlayer operators must bombard Mac users over and over in a brute-force fashion to compensate for extremely low success rates. A more somber, and probably less likely, possibility: the success rate is high enough that operators keep coming back for more. In either case, it’s likely that the help of affiliates contributes to Shlayer’s ranking.
In any event, Shlayer’s ranking is a good reason for people to remember that Flash is an antiquated browser add-on that presents more risk than benefit for the vast majority of the world. For those who must use it, they should download updates solely from https://get.adobe.com/flashplayer/.
People should never receive updates from windows that are displayed when trying to view videos or install software. The distinction can be hard for less experienced users, because Flash itself presents—or at least used to present—notifications when updates were available. People also would do well to steer clear of sites offering pirated material.