Unpatched US government website gets pwned by pro-Iran script kiddie

-
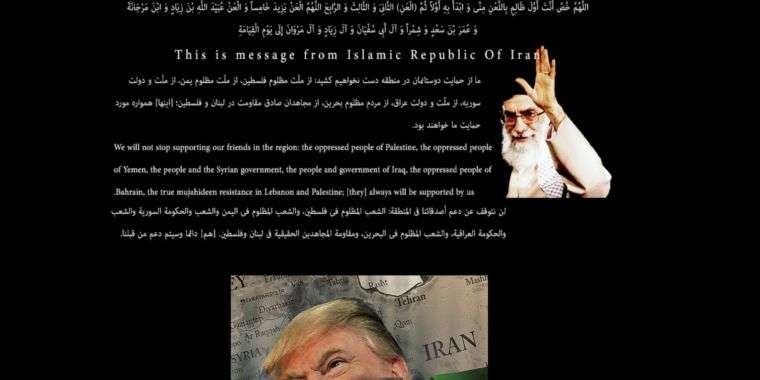
The defaced Federal Deposit Library Program website as it appeared on January 5.
-
The Federal Deposit Library Program’s home page as it appeared in November.
-
IRAN-CYBER’s scoreboard on Zone-H.
On the heels of the killing of Iranian Revolutionary Guard Corps General Qassem Soleimani by a US MQ-9 Reaper strike on January 2, the US Department of Homeland Security warned of potential cyberattacks against critical infrastructure by Iran. That warning probably didn’t apply to the website of the Federal Deposit Library Program, operated by the US Government Printing Office—which was defaced on January 4 with a pro-Iranian message and an image of a bloodied President Donald Trump being punched by an Iranian fist.
The FDLP website is no stranger to defacement attacks. As a brief analysis of the attack by a security researcher with the Twitter username @sshell_ noted, the site has been defaced twice in the last 10 years—most recently in 2014, when it was replaced with an electronic dance music video featuring a dancing cat. Based on a fingerprint of the site’s files, the site—based on the Joomla content management system—had not had its code updated since 2012. And the site had modules that used a version of Joomla’s RSForm that had been flagged 11 months ago as being vulnerable to a SQL Injection attack.
While the image depicting Trump had no metadata attached to it, another image with text had Exchangeable Image File Format (EXIF) data indicating it had been created with Adobe Photoshop CS 6 for Windows in 2015. As sshell_ noted, the image was used in a defacement reported to the “cybercrime archive” Zone-H by a user identifying themselves as IRAN-CYBER on December 2, 2015.
Zone-H offers a sort of scoreboard for defacement hackers, allowing them to report their deeds anonymously. IRAN-CYBER has reported 2,447 defacements dating back to 2015—most of them opportunistic attacks on poorly protected sites.
The FDLP site defacement was reported widely by media tying it to the threats of retaliation by Iran. The DHS’ Cybersecurity and Infrastructure Security Agency (CISA) was forced to respond to reports, with a spokesperson noting that “there is no confirmation that this was the action of Iranian state-sponsored actors.”