WireGuard on Windows early preview

-
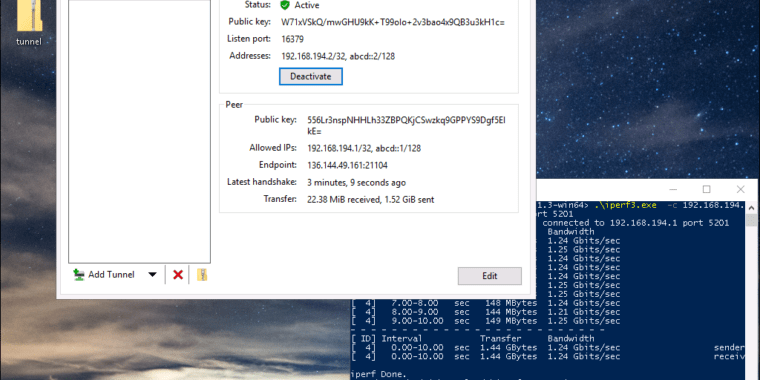
WireGuard 0.0.14 pre-alpha, running on an x1.small machine at packet.net. It’s uploading across a WireGuard tunnel at 1.2Gbps to a Linux machine, also at packet.Jim Salter
-
Here, it’s downloading across a WireGuard tunnel at 348Mbps from a Linux machine, also at packet.Jim Salter
WireGuard is a new peer-to-peer VPN technology that has the potential for greater speed, smaller attack surface, and easier configuration than commonly used and better-established VPN platforms such as OpenVPN and IPSec. It has been available on Linux, FreeBSD, macOS, Android, and even iOS for quite some time now, with Windows being the one platform frustratingly missing. There are good reasons for that—lead developer Jason Donenfeld didn’t want to inherit the problems of OpenVPN’s OpenTAP adapter code, and when he investigated Microsoft’s built-in VPN API, he didn’t like that either. So his first move was to take a giant step backwards on the Windows platform and develop an extremely simple virtual adapter that could be used not only for WireGuard, but also for other projects that might need the same kind of very basic, socket-and-tunnel functionality. This became Wintun.
For the moment, WireGuard for Windows is still in what creator Jason Donenfeld refers to as “pre-alpha,” with an alpha build due out sometime in the next week or two. The good news is, it’s an easy install now, with no dev-fu required to get it running happily on a Windows 10 (or Server 2016, as seen below) system. There are self-contained, signed MSI installers for both 64-bit and 32-bit builds there; downloading and running them just works, with no complaints from Defender about unsigned or untrusted anything. I was curious about what makes v0.0.14 “pre-alpha” rather than merely “alpha.” Donenfeld told me one reason he called it pre-alpha was to keep journalists like me (as well as the generally unadventurous) from writing about it before it’s ready.
Pressed for more detail, it became clear that he’s laser-focused on security—and Windows as a platform diverges far more radically from Linux, Android, macOS and iOS in that regard than any of them do from one another. There’s no access to Windows kernel source code, and the documentation is insufficient for his needs. As a result, he has spent hundreds of hours in a disassembler, reverse-engineering ntoskrnl.exe and ndis.sys to make absolutely sure he understands exactly what’s going on at an extremely low level most developers never bother with.
The WireGuard-Windows project maintains an attack surface document specifically documenting possible ways to attack the code, and while we were chatting on Twitter, Donenfeld finished a fascinatingly detailed mailing list post about Windows’ Network Location Awareness Signatures. All this makes it very clear that the Windows port of WireGuard isn’t really “just a port”; it’s a ground-up project in its own right, with a level of platform-specific attention to detail that would shame most Windows-native developers.
With all my questions about the current and near-future state of the project answered, I downloaded the current version of WireGuard for Windows and took it for a quick spin on a bare metal Windows 2016 instance at Packet. The short version is: it’s pretty sweet.
Once the installer for WireGuard has run, a close facsimile of the mobile interface you’d see on WireGuard for Android, iOS, or macOS pops up. You can easily import, export, activate, deactivate, or destroy tunnel configurations. Tunnel configuration can be imported either directly from a raw .conf file (format just like the ones used in text-based Linux configs in our prior coverage), or from a ZIP file which can contain multiple tunnels. The interface is barebones and offers no hand-holding, but it works very well—even including a context-sensitive text editor that catches and red-underlines many common errors, such as invalid IPv4 or IPv6 addresses.
-
You can either import a tunnel from an existing .conf or .ZIP file, or create one from scratch within the WireGuard app itself.Jim Salter
-
The built-in WireGuard editor is a nice surprise—it’s context-sensitive, and automatically highlights common errors, such as invalid IPv4 or IPv6 address formats.Jim Salter
In one last and particularly appreciated touch, it turns out that tunnel states persist across reboot—if you had a tunnel active when you restart your Windows machine, it will automatically activate itself after the reboot; there’s no need to run the UI or do anything else to restart it. Similarly, if a tunnel was deactivated at shutdown or reboot, it will still be down after the machine restarts.
Beyond all this, if you know how to use WireGuard on other platforms, you know how to use it on Windows. Connection times are still instantaneous, and the throughput is good. I achieved 1.2Gbps upload throughput across a WireGuard tunnel from the Windows 2016 machine above to a Linux machine (also at Packet). Download throughput across the tunnel capped at 380Mbps, but Donenfeld says that’s a known bug that has been fixed in master, and the improved, faster code will be available to the general public in the upcoming 0.1 alpha release.
Listing image by Jim Salter




