I’ll be passing on Google’s new 2fa for logins on iPhones and iPads. Here’s why

Google is expanding its new Android-based two-factor authentication (2fa) to people logging in to Google and Google Cloud services on iPhones and iPads. While Google deserves props for trying to make stronger authentication available to more users, I’ll be avoiding it in favor of 2fa methods Google has had in place for years. I’ll explain why later. First, here’s some background.
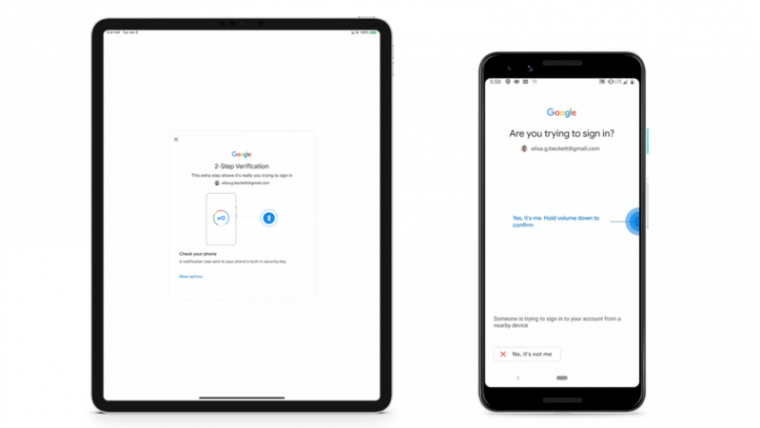
Google first announced Android’s built-in security key in April, when it went into beta, and again in May, when it became generally available. The idea is to make devices running Android 7 and up users’ primary 2fa device. When someone enters a valid password into a Google account, the phone displays a message alerting the account owner. Users then tap a “yes” button if the login is legitimate. If it’s an unauthorized attempt, the user can block the login from going through.
The system aims to tighten account security in a meaningful way. One of the key causes of account breaches is passwords that are compromised in phishing attacks or other types of data thefts. Google has been a leader when it comes to two-factor protections that by definition require something in addition to a password for someone to gain access to an account.
Among the strongest forms of 2fa available from Google are cryptographic security keys that connect to a computer’s USB slot. These keys are based on standards from the industry-wide FIDO alliance. They’re extremely reliable and virtually impossible to be phished. Later versions that used low-energy Bluetooth or near-field communication worked natively with Android devices but so far have been a nonstarter with iOS users, who complain the devices don’t always work reliably.
That has left Google scrambling for another FIDO-sanctioned way for the masses to do 2fa. And that’s where Android built-in keys come in. Unfortunately, there are key drawbacks to this method as well. First, it relies on Bluetooth, and all its maddening glitches, for the phone to communicate with the macOS, Windows 10, or Chrome OS device the user is logging in to. Second, it also works only when people log in to an account using Google’s Chrome browser. Other browsers and apps are out of luck. Another shortcoming was that Android keys weren’t available to users logging in from an iOS device.
On Wednesday, Google is addressing this last drawback with a new method that brings Android keys to iPhone and iPad users. It relies on the Google Smart Lock app running on the iOS device that communicates over Bluetooth with the built-in key stored on the user’s Android phone or tablet. (The app, which is also used to make FIDO-based crypto keys work with iOS devices, has user ratings of just 2.2 out of 5.) Google has additional instructions here. Company representatives declined to provide interviews for this post.
Thanks, but no thanks
I spent about 90 minutes trying to get the method to work between an iPad mini and a Pixel XL. I had no trouble setting up Android’s built-in key and using it to authenticate logins from a macOS computer to both a personal Google account and a work account provided by G Suite. Alas, I was never able to get the Android keys to work when logging in to either account on the iPad mini. It was a frustrating experience, but at least it was progress. Ars Reviews Editor Ron Amadeo told me he was unable to get even the Android piece to work when he tried several weeks ago.
I won’t rule out the possibility that the failure is at least in part the result of user error. But that’s not the point. If people from a tech site struggle, so, too, will Aunt Mildred or Uncle Frank in Poughkeepsie. And given Bluetooth’s above-mentioned quirks, it seems entirely plausible that our inability to get Android’s built-in keys to work was the result of a failure of the devices to connect over this wireless channel.
And as long as we’re talking about Bluetooth deficiencies, let’s not forget that Google recently warned that the Bluetooth Low Energy version of the Titan security key it sells for two-factor authentication can be hijacked by nearby attackers. The weakness doesn’t automatically mean Bluetooth is insecure, but it does suggest that the channel may be less suited for highly sensitive security protocols than some engineers recognize. So for the time being, I have no plans to use Android keys when logging in to Google on my iOS devices. Instead, I’ll continue to use Duo Mobile’s authenticator feature (Google Authenticator works almost identically), as I have for a while now. This mechanism isn’t perfect. The one-time token numbers are short-lived, but they can still be obtained by quick-moving attackers who enter credentials into a real Google account immediately after a target enters them in to a look-alike phishing site. That scenario may help explain how Iranian hackers recently managed to bypass 2fa protections offered by Yahoo Mail and Gmail.
Another 2fa option for iOS users is Google prompt, which has been available for more than a year. Unfortunately, that protection, too, can be abused by quick-acting phishers.
So thanks, Google, for trying so hard to bring easy-to-use 2fa to more users. But I’ll pass on this latest offering until the industry gets this mess sorted out.




