Serial publisher of Windows 0-days drops exploits for 3 more unfixed flaws

A serial publisher of Microsoft zeroday vulnerabilities has dropped exploit code for three more unpatched flaws, marking the seventh time the unknown person has done so in the past year.
Technical details of the vulnerabilities, along with working proof-of-concept exploits, are the work of someone using the moniker SandBoxEscaper. A local privilege-escalation vulnerability in the Windows Task Scheduler that was disclosed on Tuesday allows an authenticated attacker to gain SYSTEM privileges on an affected system. On Thursday, the person released a privilege escalation code that exploits a bug in the Windows Error Reporting service. Attackers can use it to modify files that would normally be off limits. A third exploit, which was also released Wednesday, works against Internet Explorer 11 and allows attackers to execute a JavaScript that runs with higher system access than is normally permitted by the browser sandbox.
Decent deal
Like the other exploits SandboxEscaper has published over the past year—including this one Ars covered last August and this one from last October—the three recent ones don’t allow attackers to remotely execute malicious code. Still, as security defenses in recent versions of Windows and other operating systems have improved, the value of these types of exploits has grown, since they are often the only way to bypass security sandboxes and similar protections. Despite some limitations in the exploit that were transparently noted by SandBoxEscaper, the disclosures are significant if they work as purported against fully patched versions of Windows 10.
“Any new privilege escalation on native Windows 10 is a pretty decent deal as most vulnerabilities are on applications that you put on top of the OS rather than in the OS itself,” Charles Dardaman, a security researcher in Dallas, told Ars. “If an attacker had an RCE or some other way, like phishing, that gave low-level access to a machine, they could then use one of these attacks to escalate to Admin.”
In March, Google reported that a then-unpatched privilege-escalation vulnerability in older versions of Windows was being used alongside an unrelated exploit in the Chrome browser. On its own, neither exploit was able to do much damage, thanks to the defense-in-depth mitigations built into Windows and Chrome. Together, however, the exploits allowed hackers to remotely execute malware of their choice. Dardaman said that the two privilege-escalation vulnerabilities SandboxEscaper published over the past 24 hours are likely to have similar capabilities when combined with the right additional exploit.
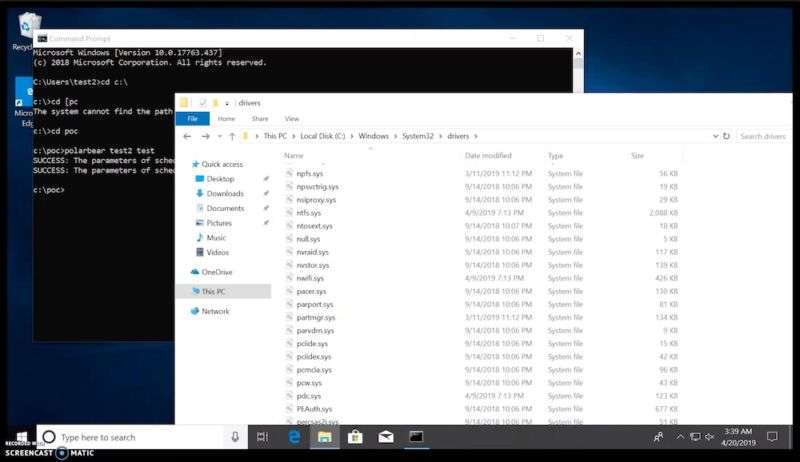
In Tuesday’s disclosure, SandboxEscaper wrote that the Task Scheduler vulnerability works by exploiting a flaw in the way the Task Scheduler processes changes to discretionary access control list permissions for an individual file. An advisory published Wednesday by US Cert confirmed that the exploit worked against both 32-bit and 64-bit versions of Windows 10.
Below is video of the exploit in action:
Here’s a demo of a Windows 10 privilege escalation zeroday that US Cert has confirmed works against Windows 10. Microsoft has yet to comment on it. pic.twitter.com/hFP05fqPRM
— Dan Goodin (@dangoodin001) May 22, 2019
Microsoft representatives have yet to comment on the disclosures this week, and researchers have yet to confirm the two exploits published Wednesday work against fully-patched Windows 10. Given SandboxEscaper’s track record, people should assume the exploits work as billed and stay apprised of any new updates or bulletins that may be published in the coming days.