Hackers abuse ASUS cloud service to install backdoor on users’ PCs

ASUS’ update mechanism has once again been abused to install malware that backdoors PCs, researchers from Eset reported earlier this week. The researchers, who continue to investigate the incident, said they believe the attacks are the result of router-level man-in-the-middle attacks that exploit insecure HTTP connections between end users and ASUS servers, along with incomplete code-signing to validate the authenticity of received files before they’re executed.
Plead, as the malware is known, is the work of espionage hackers Trend Micro calls the BlackTech Group, which targets government agencies and private organizations in Asia. Last year, the group used legitimate code-signing certificates stolen from router-maker D-Link to cryptographically authenticate itself as trustworthy. Before that, the BlackTech Group used spear-phishing emails and vulnerable routers to serve as command-and-control servers for its malware.
Late last month, Eset researchers noticed the BlackTech Group was using a new and unusual method to sneak Plead onto targets’ computers. The backdoor arrived in a file named ASUS Webstorage Upate.exe included in an update from ASUS. An analysis showed infections were being created and executed by AsusWSPanel.exe, which is a legitimate Windows process belonging to, and digitally signed by, ASUS WebStorage. As the name suggests, ASUS WebStorage is a cloud service the computer-maker offers for storing files. Eset published its findings on Tuesday.
The abuse of legitimate AsusWSPanel.exe raised the possibility the computer-maker had fallen to yet another supply-chain attack that was hijacking its update process to install backdoors on end-user computers. Eventually, Eset researchers discounted that theory for three reasons:
-
- The same suspected update mechanism was also delivering legitimate ASUS WebStorage binaries
- There was no evidence ASUS WebStorage servers were being used as control servers or served malicious binaries, and
- The attackers used standalone malware files instead of incorporating their malicious wares inside ASUS’s legitimate software
As the researchers considered alternative scenarios, they noted that ASUS WebStorage software is susceptible to man-in-the-middle attacks, in which hackers controlling a connection tamper with the data passing through it. The researchers made this determination because updates are requested and transferred using unencrypted HTTP connections, rather than HTTPS connections that are immune to such exploits. The researchers further noticed that the ASUS software didn’t validate its authenticity before executing. That left open the possibility the BlackTech Group was intercepting ASUS’ update process and using it to push the Plead instead of the legitimate ASUS file.
The researchers also observed that most of the organizations that received the Plead file from ASUS WebStorage were using routers made by the same manufacturer. The routers, which Eset declined to identify while it’s still investigating the case, have administrator panels that are Internet accessible. That left open the possibility a MitM attack was being caused by malicious domain name systems settings being made to the routers or something more complex, such as tampering with iptables.
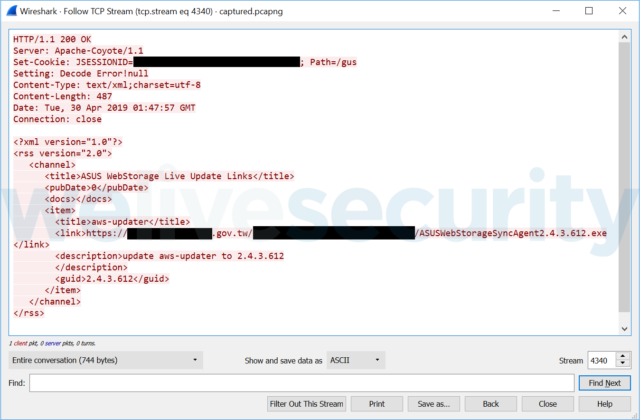
Eset’s working theory then shifted from the BlackTech Group breaching ASUS’ network and performing a supply-chain attack to the attackers performing a MitM attack on ASUS’ insecure update mechanism. Indeed, as documented below in a screenshot of a captured communication during a malicious ASUS WebStorage software update, attackers replaced the legitimate ASUS URL with one from a compromised Taiwanese government website.
In an email, Eset Senior Malware Researcher Anton Cherepanov said the captured communication isn’t proof of a MitM.
“It’s possible that attackers gained access to ASUS WebStorage servers and pushed XML with malicious link only to small number of computers,” he wrote. That’s why we say it’s still possible. We can’t discount this theory.”
But for the reasons listed above, he believes the MitM scenario is more likely.
In all, Eset has counted about 20 computers receiving the malicious ASUS update, but that number includes only company customers. “The real number is probably higher if we consider targets that are not our users,” Anton Cherepanov, a senior malware researcher at Eset, told Ars.
Once the file is executed, it downloads an image from a different server that contains an encrypted executable file hidden inside. Once decrypted, the malicious executable gets dropped into the Windows Start Menu folder, where it’s loaded each time the user logs in.
It’s surprising that even after the serious supply-chain attack estimated to have infected as many as 1 million users, the company was still using unencrypted HTTP connections to deliver updates. Ars sent ASUS media representatives two messages seeking comment for this post. So far they have yet to respond. In a blog post sent over an unencrypted HTTP connection, ASUS reported a “WebStorage security incident” that reads:
ASUS Cloud first learned of an incident in late April 2019, when we were contacted by a customer with a security concern. Upon learning of the incident, ASUS Cloud took immediate action to mitigate the attack by shutting down the ASUS WebStorage update server and halting the issuance of all ASUS WebStorage update notifications, thereby effectively stopping the attack.
In response to this attack, ASUS Cloud has revamped the host architecture of the update server and has implemented security measures aimed at strengthening data protection. This will prevent similar attacks in the future. Nevertheless, ASUS Cloud strongly recommends that users of ASUS WebStorage services immediately run a complete virus scan to ensure the integrity of your personal data.
The post doesn’t say what those security measures are. It also makes no mention of Eset’s finding that the service was abused to install malware. Until independent security experts say the site is safe to use, people would do well to avoid it.