“Yelp, but for MAGA” turns red over security disclosure, threatens researcher

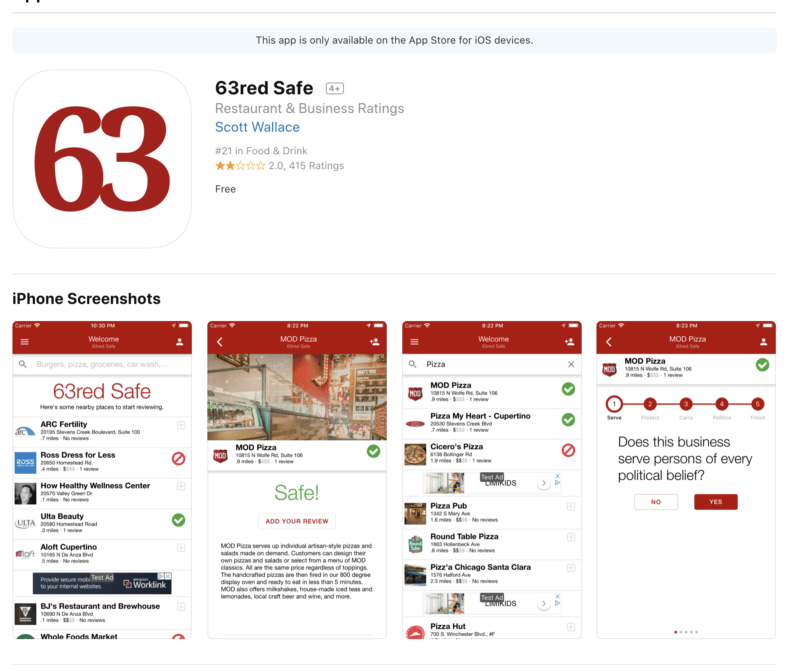
A new application from the “conservative news” site 63red, called 63Red Safe, is advertised as a sort of “Green Book” for the MAGA set. It lets users rate local businesses “from a conservative perspective,” according to the app’s Google Play listing, “helping insure[sic] you’re safe when you shop and eat!” And in this case, “safe” means freedom to wear “Make America Great Again” clothing without having to bear verbal challenge.
The app rates the safety of a business based on user’s input on four factors:
—Does this business serve persons of every political belief?
—Will this business protect its customers if they are attacked for political reasons?
—Does this business allow legal concealed carry under this state’s laws?
—Does this business avoid politics in its ads and social media postings?
But the safe space for 63red founder Scott Wallace was violated quickly when French security researcher Elliot Alderson discovered some fundamental security flaws in Safe’s architecture—making it not so safe.
Because the application is build in React Native, a JavaScript- and JSX-based scripting language that basically turns Web apps into “native” Apple iOS and Android applications, the entire architecture of the application is available to anyone who downloads and unpacks it. And in that code, Alderson discovered a few things:
- Wallace had left his username, email, and a plaintext password in the code—twice.
- There is no authentication for any of the application programming interface calls, so someone could spoof any user—essentially giving them administrative access to the API.
- All of the APIs are clearly defined as URLs in the source code.
- By using the “Get user by ID” API call, someone could retrieve the user name, email, ban status, and other details on each user account. Passwords were not in this data, but the entire user database could be retrieved by iterating through all the possible first letters or digits of an account ID.
- Any user could be blocked using an HTTP Post to the “block” API.
Alderson shared these details in a Twitter thread:
This app uses a language called @reactnative. Get the original source of the app is super easy. Because he is nice, the developer of the hardcoded his credentials in the source code… twice… pic.twitter.com/DWwAvagSs5
— Elliot Alderson (@fs0c131y) March 12, 2019
Wallace’s response was not magnanimous: “No lost passwords, no breach of database, no data changed, minor problem fixed. We’re angry by the attempt, FBI notified,” Wallace posted to Twitter, along with a link to a Medium post in which he stated:
We see this person’s illegal and failed attempts to access our database servers as a politically motivated attack, and will be reporting it to the FBI later today. We hope that, just as in the case of many other politically motivated Internet attacks, this perpetrator will be brought to justice, and we will pursue this matter, and all other attacks, failed or otherwise, to the utmost extent of the law. We log all activity against all our servers, and will present those logs as evidence of a crime.
Alderson said he never attempted to change any data. “I did not hack your app, I read the available source code, and I used your unauthenticated APIs. It’s equivalent to use [sic] your app,” he responded to Wallace. “By threatening me, a security researcher, you are threatening the whole infosec community. I’m a professional and I’m not hiding. I’m staying at your disposal if needed. Btw, how did you fix the issue without updating your app?”




