
Google Play malware used phones’ motion sensors to conceal itself

Malicious apps hosted in the Google Play market are trying a clever trick to avoid detection—they monitor the motion-sensor input of an infected device before installing a powerful banking trojan to make sure it doesn’t load on emulators researchers use to detect attacks.
The thinking behind the monitoring is that sensors in real end-user devices will record motion as people use them. By contrast, emulators used by security researchers—and possibly Google employees screening apps submitted to Play—are less likely to use sensors. Two Google Play apps recently caught dropping the Anubis banking malware on infected devices would activate the payload only when motion was detected first. Otherwise, the trojan would remain dormant.
Security firm Trend Micro found the motion-activated dropper in two apps—BatterySaverMobi, which had about 5,000 downloads, and Currency Converter, which had an unknown number of downloads. Google removed them once it learned they were malicious.
The motion detection wasn’t the only clever feature of the malicious apps. Once one of the apps installed Anubis on a device, the dropper used requests and responses over Twitter and Telegram to locate the required command and control server.
“Then, it registers with the C&C server and checks for commands with an HTTP POST request,” Trend Micro researcher Kevin Sun wrote. “If the server responds to the app with an APK command and attaches the download URL, then the Anubis payload will be dropped in the background.” The dropper then tried to trick users into installing the app using the fake system update shown below:
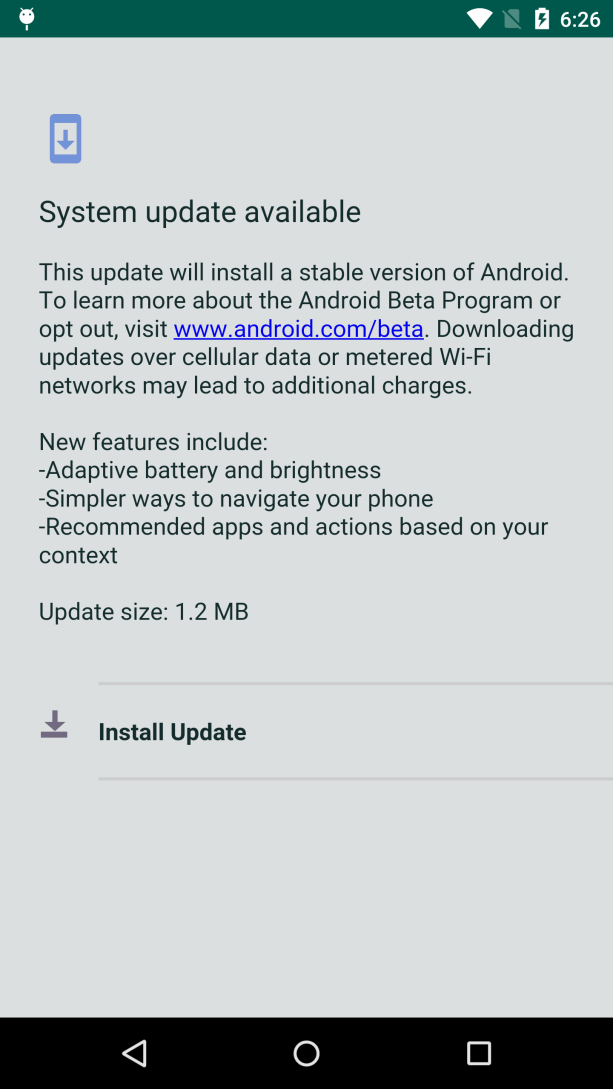
Once Anubis was installed, it used a built-in keylogger that can steal users’ account credentials. The malware can also obtain credentials by taking screenshots of the infected users’ screen. Sun continued:
Our data shows that the latest version of Anubis has been distributed to 93 different countries and targets the users of 377 variations of financial apps to farm account details. We can also see that, if Anubis successfully runs, an attacker would gain access to contact lists as well as location. It would also have the ability to record audio, send SMS messages, make calls, and alter external storage. Anubis can use these permissions to send spam messages to contacts, call numbers from the device, and other malicious activities. Previous research from security company Quick Heal Technologies shows that versions of Anubis even function as a ransomware.
The researcher provided the following screenshot showing some of the financial apps Anubis targets:
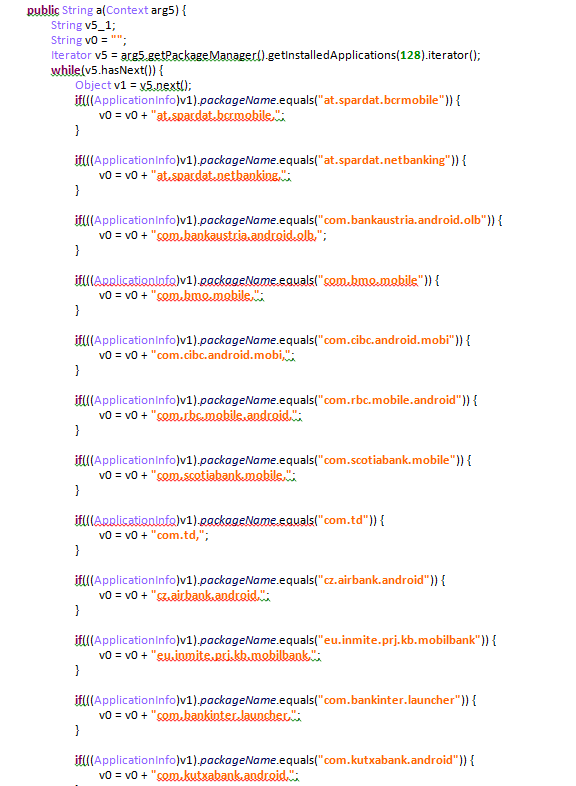
There are two takeaways from the report. The first is that the quality of malicious Android apps is improving. The second is that Android users should continue to think carefully before downloading and installing apps on their devices. The purported benefit of both of these now-removed apps was minimal. People are better off sticking to a small number of apps from well-recognized developers.




